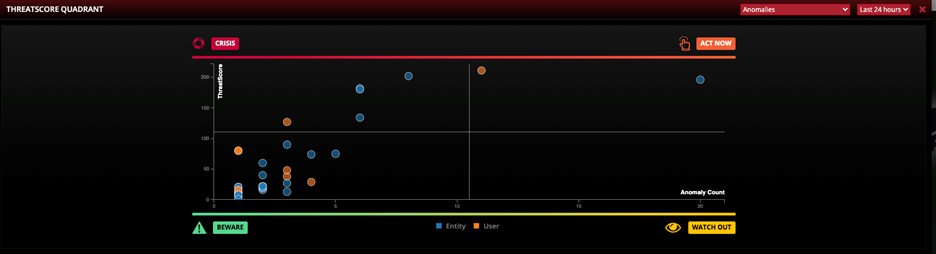
How does LinkShadow speed up Incident response time?
- Calculated Threat risk assessment of entities based on information received from the external third-party security systems.
- Provide a single pane of glass in the investigation window that displays LinkShadow detections and detections from the external systems all in the same view, thereby allowing the SOC analyst to perform quick co-relation.
- Take immediate mitigation action like isolation or block.
- Verify with the application team about the genuineness of the detected event.
- Verify with the system user about the genuineness of the detected event.