How Does LinkShadow Provide Investigation Capabilities post-Breach?
- Calculating threat risk assessments of entities based on information received from external third-party security systems.
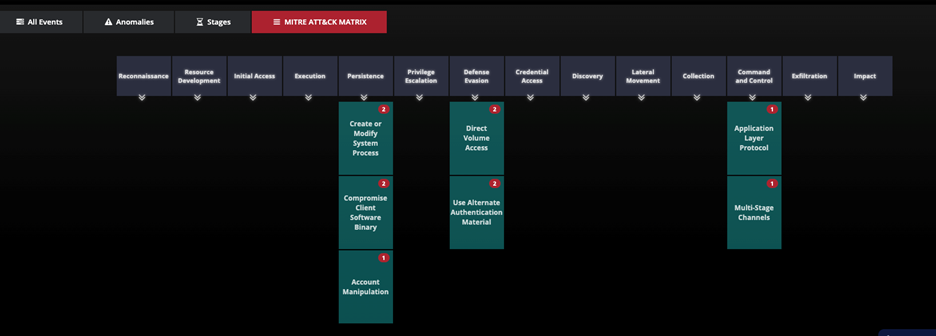
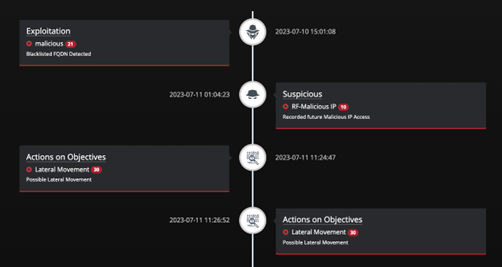
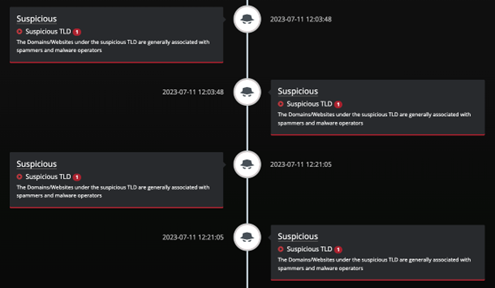
- Providing a single pane of glass in the investigation window that displays LinkShadow detections and detections from external systems all in the same view, thereby allowing SOC analysts to perform quick correlation.
- Taking immediate mitigation actions like isolation or blocking.
- Verifying with the application team the genuineness of the detected event.
- Verifying with the system user the genuineness of the detected event.
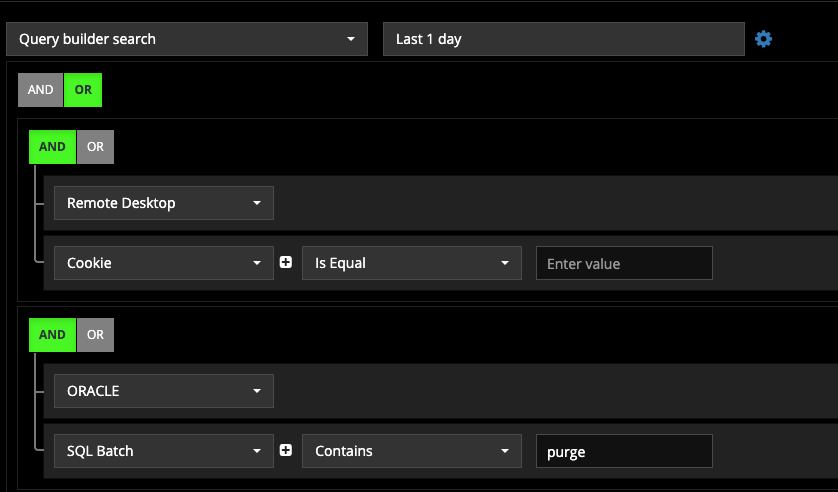
- For a specific period, show the Oracle DB traffic destined to the Database server which has the purge command.
- Show all the filenames that were part of SMB file access related to a specific user.
- Show all connections that had a data transfer and were destined to the Internet from the corporate network.
- Show all Remote Desktop connections that were destined to the Internet from the corporate network.